What is cloaking and how to cloak correctly?
Cloaking is a technology for replacing content that is shown when clicking on a link in an advertisement. We also know that a cloaca is a tool for separating traffic. The very term "cloaking" is not derived from the word "cloaca". In English, these two words are spelled and read differently. Cloaking means to hide or disguise.
Why should a webmaster use a cloaca?
The reason is the fact that large traffic exchanges, as a rule, strictly approach the moderation of ads, which could prevent from going there with very profitable offers, especially when it comes to gray hat and black offers. And in order to still get access to a large high-quality traffic and earn money, we send bots and moderators to a specially prepared white page, and the target audience to our original landing page.
We also talk about cloaking in detail in our video.
We identify 3 elements that cloaking includes:
- White Page is a page that fully complies with the rules of the exchange without any aggressive presentation. The simplest form in which White Page can be presented is an informational article with a link to the source site related to the topic of the offer (without a hint of the sale of goods), or you can simply take it to a white site with a thematic post so that there are no suspicions. Also, in general, you can divert inappropriate traffic to a page with a «404 error», for example.
- Black Page is a landing page where the user will be actively pushed to buy and influence their psyche with all sorts of facts, statistics and WOW effects.
- Cloaca is software for cloaking, namely trackers or special services.
We talked about trackers in more detail in this video.
The possibility of cloaking is not always available. Setting them up is quite simple: when creating a campaign, we specify the conditions under which traffic will be redirected to White, under which to the landing page, and finally all is done. As for special services, there are paid and free ones, and unlike trackers, they have deeper filtering options, collect the necessary databases, there are even services that analyze devices using their neural networks, and many of them have integration with popular trackers too.
But cloaking isn’t limited to one purpose. In addition to passing moderation, with its help we can:
- Use it to work with fraudulent traffic
- Use it to work with funnels
- Use it for the confidential side of traffic handling
By the way, Cloaking itself is also not a permitted procedure. Therefore, when such manipulations are detected, accounts are blocked, even if some time has already passed since the launch, don’t forget about it! Therefore, it is better to practice this method on new accounts and consumables.
How to set up Cloaking using the Keitaro tracker and the HideClick service
So, to set up Cloaking in Keitaro, click "Settings".

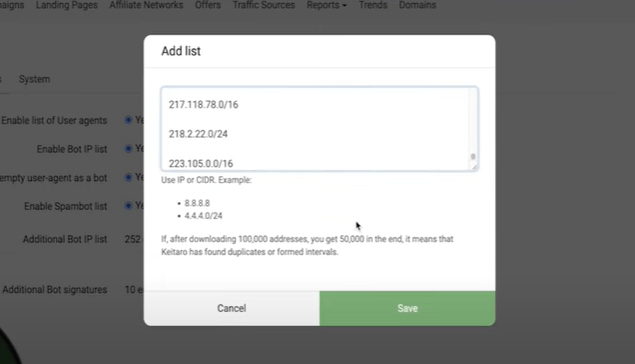
In the “List of bots” item, put down all the items like this, and add a list of bots.
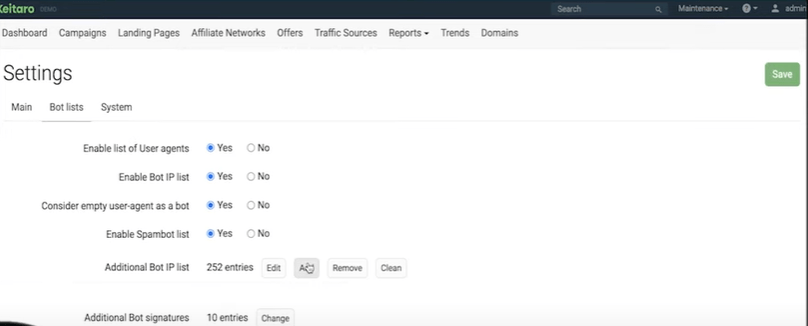
The list of bots can be found here.
Next, we move on to creating a new campaign and in it, we will create 3 streams.
The first stream will send irrelevant traffic to White Page, so let's name it so that it's clear for everyone - "White Page". Then, set the stream type - “Forced”.
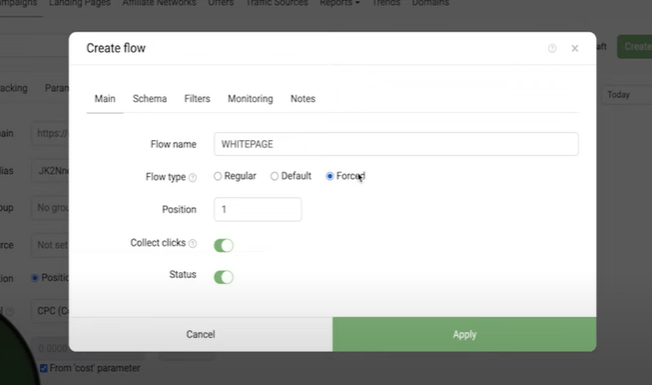
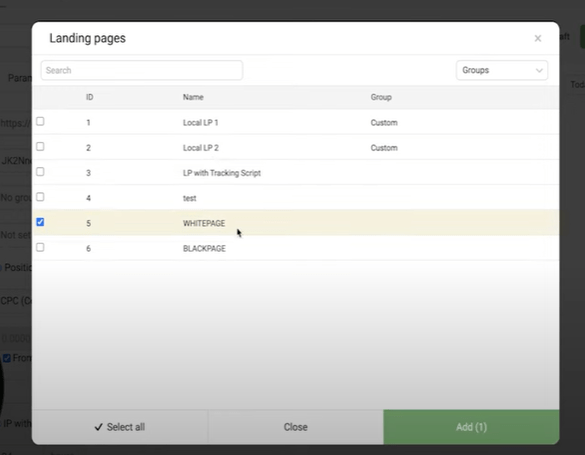
In the "Scheme" tab, add a White Page where we will send all we need.
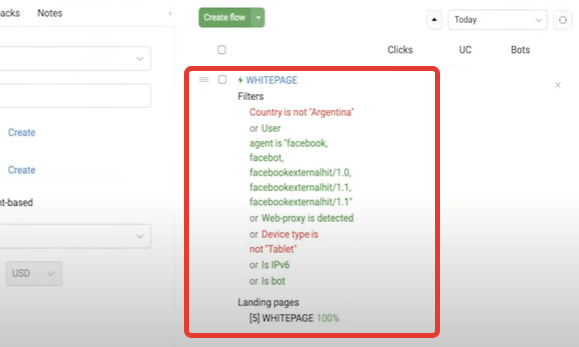
In the “Filter” tab, select the “OR” item, and then add the following filters: bot, IPv6, device type (it is better to specify irrelevant devices here), proxy, User Agent (copy the list), countries (here we can specify the target country and put “IS NOT” to filter out unnecessary GEOs). It's done, click "Apply".
Next, we create a second stream for relevant traffic. We will call it “Buyers” or “Black Page”, select the stream type as "Regular".
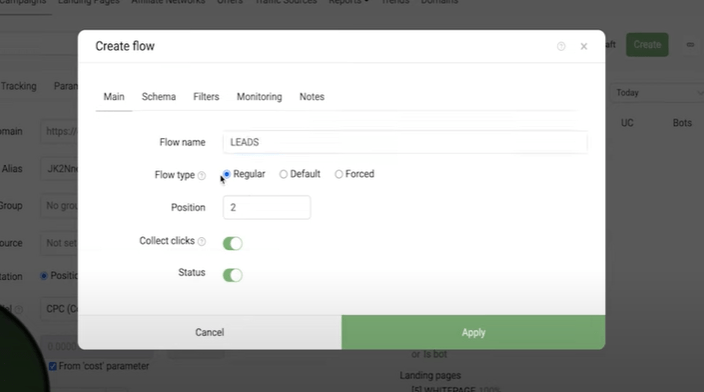
In the “Schema” tab, we indicate our offer, which should already be set up in Keitaro, or a direct URL, if you need to drive to it.
Then, go to “Filter” and put down the conditions we need, device type, GEO, operating systems, cities, etc.
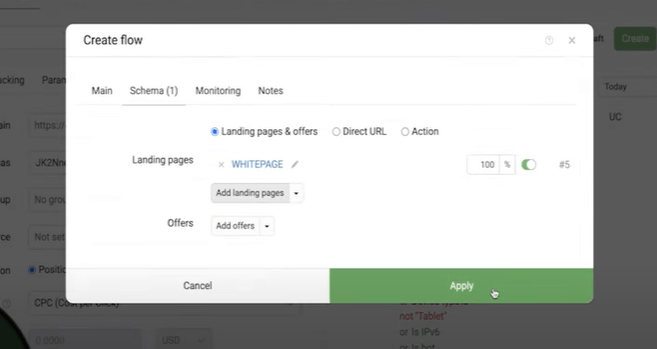
And now we create the 3rd stream, which will deal with the traffic that will not be determined by the software from the first two.
We call it again as convenient and set the type of flow - "Default". In the Schema tab, we load our White page. We save the campaign, go to the integration tab.
We set KClient PHP as the integration method, after which we copy the code and paste it at the very beginning of the code in the index.php file of our white page and save it. Then, download the kclick_client.php file and place it in the root of the domain.
Let's look at the process in HideClick
In the main menu of the service, select the "Download" item and the PHP sub-item.
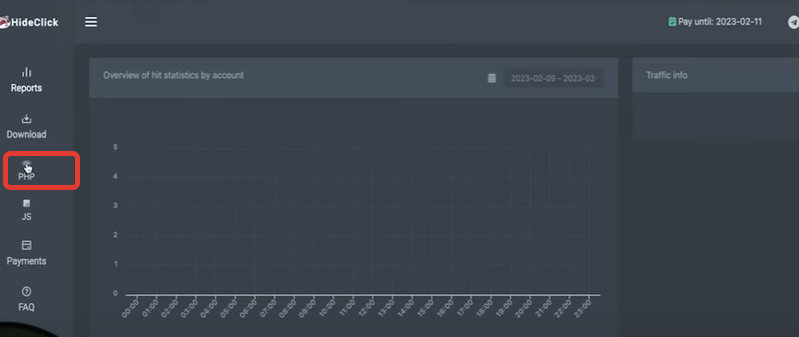
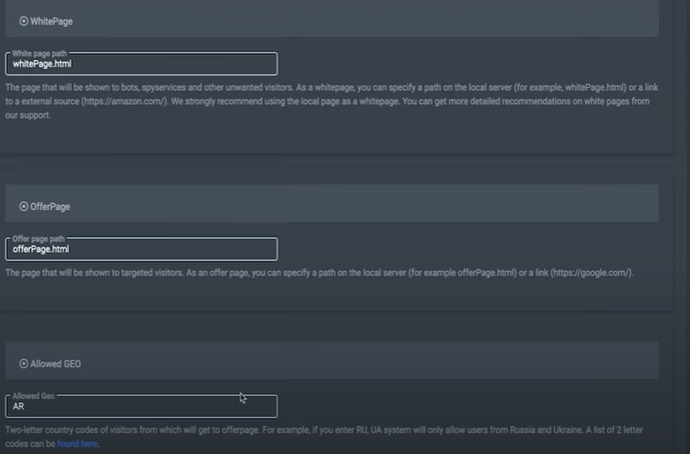
Next, fill in these three fields:
- here we copy the path to the folder with our White
- here is the path to the folder with Black
- here GEO with which we will work
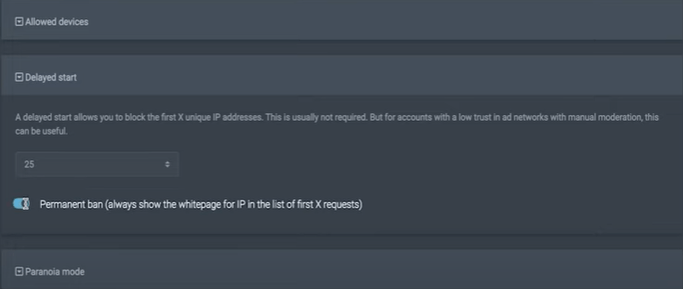
Further, in the item "Allowed devices", we leave the relevant ones for us. Also, in the next section, we can set up a BAN for the first visitors to the page. We set their number ourselves. This item allows you to play it safe in case of manual moderation.
After that, scroll down and download the INDEX.PHP file.
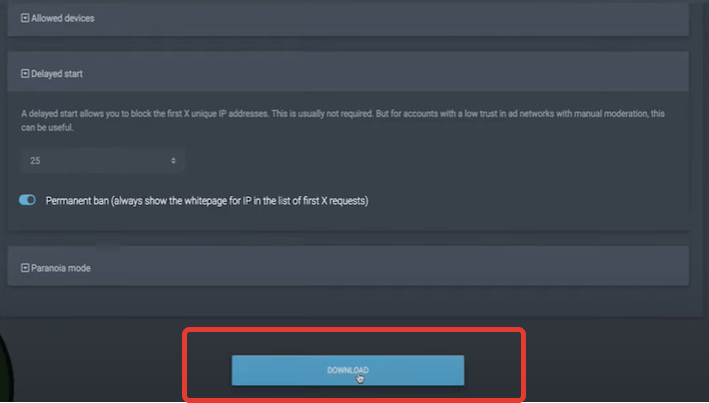
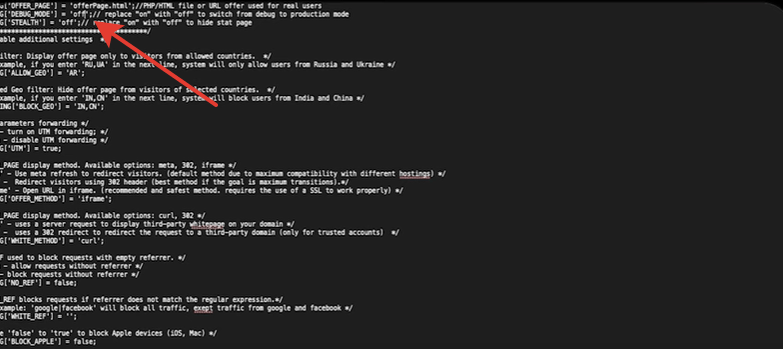
We upload this file to the domain and open it. Here in this line "On" needs to be changed to "OFF" and everything is done.
How to break through the cloak!?
Our Cloak is ready. And now as you know how the mechanism works as a whole, let's talk about how to break through this cloak. What is it for? In order to get access to other people's funnels entirely, optimize them and drive them into a plus. For example, with the help of the Spy-service, we found a creative and stumbled upon White.
We talk more about Spy - services in this video. So, now our task is to disguise ourselves as the target user. In most cases, it is enough for us to acquire the mobile IP of the target GEO. Therefore, the first step is to buy a proxy of the required GEO.
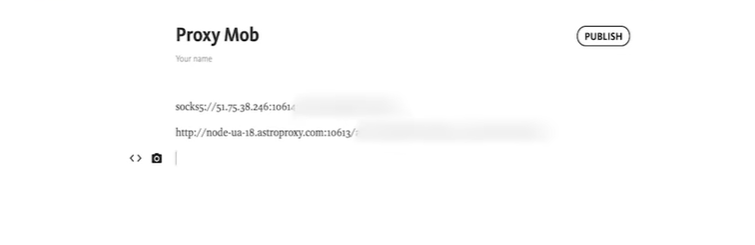
Then, open the antidetect browser and enter the data of our mobile proxy into it.
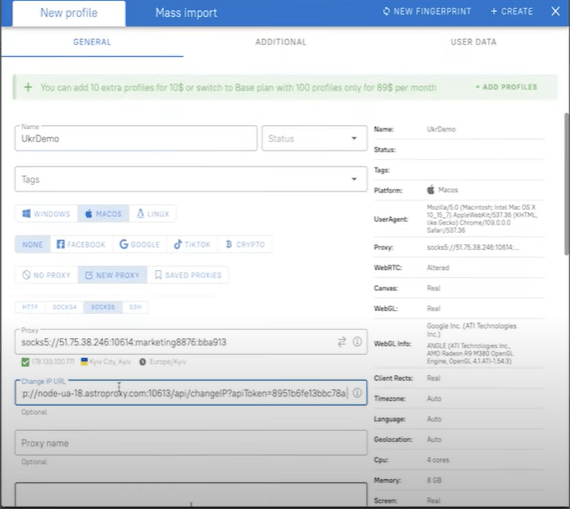
To increase the chances of breaking through, we can add such a part before our link, and encode the link itself, so that in the end it turns out like this.

This is necessary in case a filter is set in the cloak by referer, that is, to the source of the transition.

Then, in the prepared browser profile, follow the prepared link.
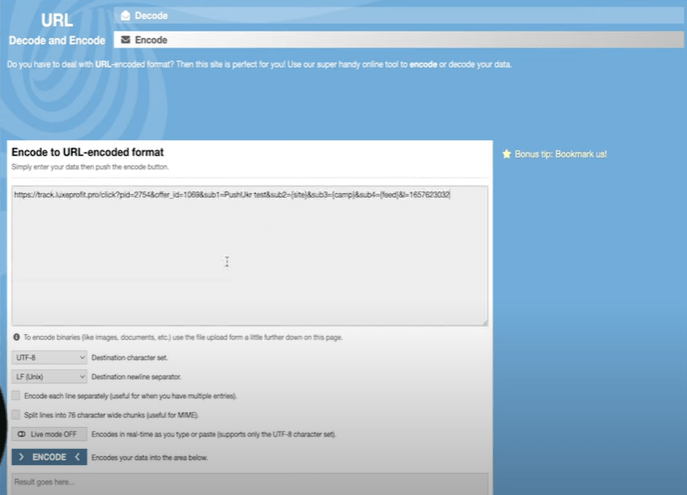

Congratulations, we just punched through someone's cloak.
Conclusion
We have figured out what cloaking is, how it is configured in the most popular tools of affiliates, and also have learned how we can breakthrough other people's cloak in order to see working links that are carefully hidden from prying eyes.
Want to start with nutra? Have questions about the case-study?
All the nutra is discussed now 24/7 in the telegram chat Nutra Affiliate Community
Quick help for beginners
Sweet cases for motivation
Exclusive bonuses from partners $$$$
Intelligent moderators and all support for affiliate network in one place








I really need help to of Dr cash affiliate marketing please my people
For assistance with this, please contact your personal manager or go to https://dr.cash/